
On Tuesday, the world witnessed another wave of hair-raising cyber-attacks that hit computer servers in Ukraine and spread internationally across Europe to reach the United States, Australia and even India. Computer experts have traced the origin of the vicious malware and have identified the first host to be an international steel company located in Ukraine, called “Petya”. Giant anti-virus company ESET stated that more than half of the attacks took place in Ukraine after the company had collected data from its global sensors and clients.
Petya Ransomware cyber-attack has caused calamitous damage around the world. ATM machines have completely stopped working in Ukraine’s capital city. Computer systems at the old Chernobyl nuclear plant were down because of the attack and workers had to manually monitor radiation levels. In addition, attack affected many companies around the world, including: Maersk, a huge shipping conglomerate in Denmark, a large pharmaceutical company in USA called “Merck” as well as Cadbury’s factory in Australia.
According to the government of Ukraine, many banks, ministries and metro systems were severely damaged by Petya virus. In Europe, giant companies such as: Rosneft in Russia, Saint-Gobain in France and Britain’s largest advertising agency WPP were among the victims to the Petya Ransomware cyber-attack.
In Australia, companies were urged by the government to make sure that security updates are installed and infected computer systems are quarantined. Dan Tehan, the cybersecurity minister said:
“This ransomware attack is a wake-up call to all Australian businesses to regularly back up their data and install the latest security patches,” […]“We are aware of the situation and monitoring it closely.”
In the United States, the Department of Homeland Security was infected by the virus. Department spokesman Scott MacConnell said in a statement:
“The Department of Homeland Security is monitoring reports of cyberattacks affecting multiple global entities and is coordinating with our international and domestic cyber partners.”
The Petya cyberattack took place one day before Ukraine’s holiday celebration of its first constitution after its independence from the Soviet Union in 1996. The attack is considered to be the most advanced and most sophisticated among the series of cyber stacks carried out by the Shadow Brokers. Petya malware hacking tool is largely similar to its predecessor WannaCry Ransomeware as it also demands large ransoms to be paid in order for system owners to get access to their computer systems once more. It also uses Eternal Blue, the same hacking tool stolen from the NSA (National Security Agency) and was also used in the Ransomware attack last May.
“The N.S.A. needs to take a leadership role in working closely with security and operating system platform vendors such as Apple and Microsoft to address the plague that they’ve unleashed,” said IDT’s global chief information officer, Golan Ben-Oni.
Eternal Blue was easily used to hack into Windows-based operating systems due to vulnerability in the Windows software. Microsoft was able to fix this flaw last March, however, due to the severity of the damage caused by the WannaCry virus, thousands of users were unable to download that fix.t
“Just because you roll out a patch doesn’t mean it’ll be put in place quickly.” […] “The more bureaucratic an organization is, the higher chance it won’t have updated its software,” said Carl Herberger, Radware’s vice president for security.
It is widely suspected that Russian hackers are behind this bloodcurdling cyber-attack. Officials in Ukraine are already placing the responsibility of this vile attack on Russia, despite the fact that many Russian companies, banks and news portals have fallen victims to the Petya virus. RBC news portal said that Home Credit Bank, one of Russia’s biggest banks and Evarez the giant steel manufacturing company which has over 80,000 employees have all been affected by the Petya Ransomware virus.
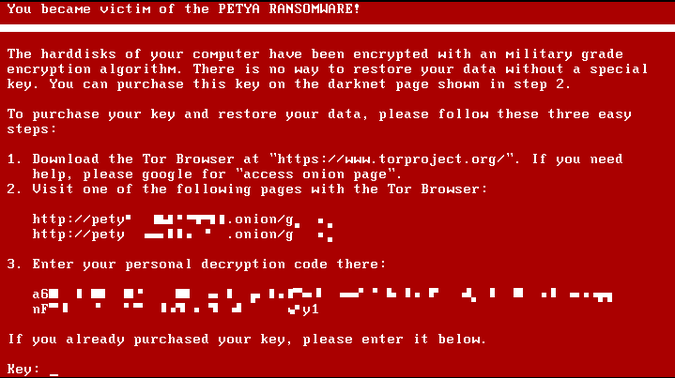
In Russian, “Petya” means “Little Peter” which has led to speculations that the name of the virus could be a reference to a symphony composed by Sergei Prokofiev called “Peter and the Wolf” which revolves around a boy capturing a wolf. It is also said that Petya Ransomware was put for sale on the Dark Web which means that the virus could be launched by anybody with a single-click of a mouse to completely lock down any person’s computer, and then demand a ransom of $300 in Bitcoin to decrypt it. Janus Cybercrime Solutions are the developers behind the Petya Ransomware virus and every time a person pays to the ransom, they get their share. According to records online, about 30 victims paid the ransom, but it is still not clear if they got access to their computer systems or not.The real intention behind this attack is very questionable by many cybersecurity analysts.
“It’s entirely possible that this attack could have been a smoke screen,” said, the managing director of global incident response at Accenture Security. “If you are an evildoer and you wanted to cause mayhem, why wouldn’t you try to first mask it as something else?”


